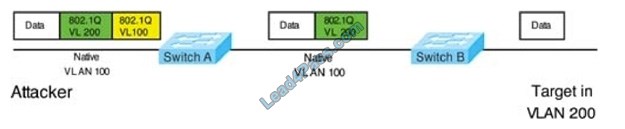
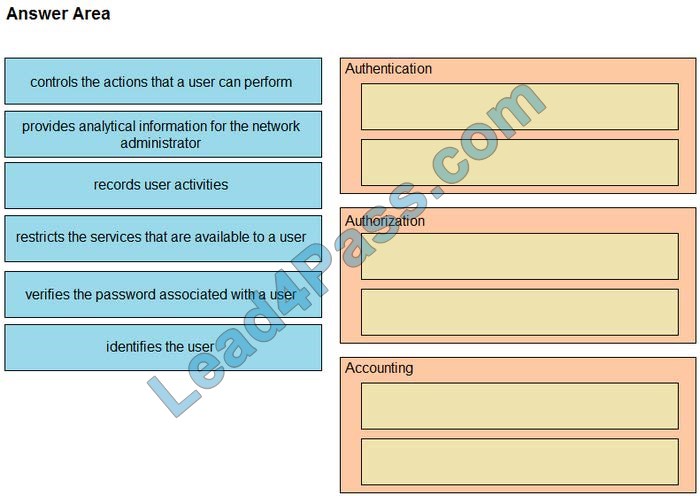
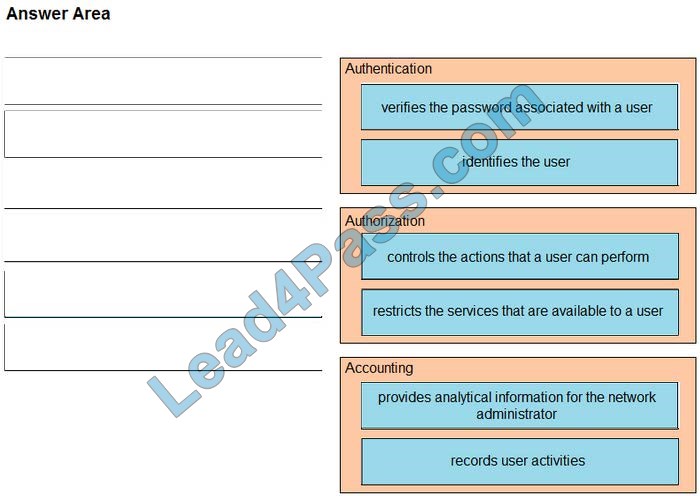
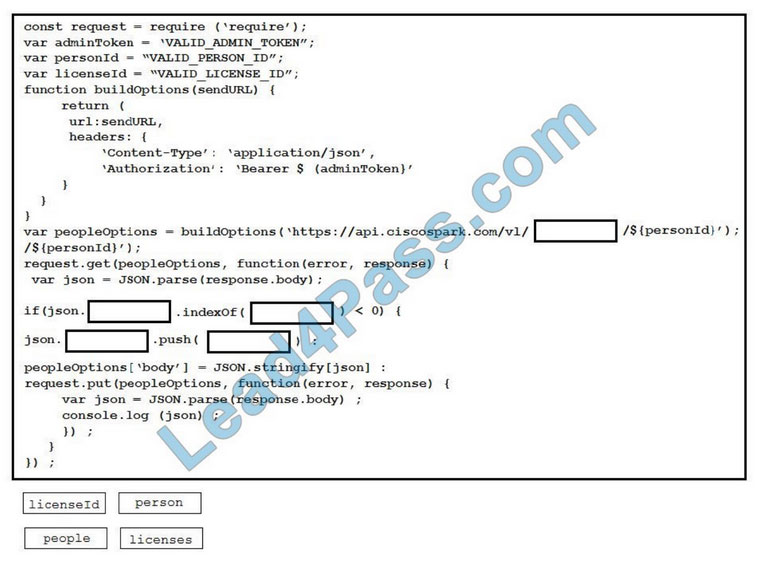
leads4pass has shared the latest 300-725 dumps exam questions and answers more than once, and today continues to share some free 300-725 exam questions and answers to help all candidates progress.
leads4pass has also helped candidates pass the CCNP Security 300-725 Securing the Web with Cisco Web Security Appliance (SWSA) certification exam more than once because they use
Full 300-725 dumps with PDF and VCE: https://www.leads4pass.com/300-725.html (60 Q&A).
Check out the CCNP Security 300-725 PDF exam questions and answers shared for free:
https://drive.google.com/file/d/1AGxV1yasc5xeNeGayahQYmy0EtICiLRy/
Read the CCNP Security 300-725 exam questions and answers shared online today:
| Number of exam questions | Exam name | From | Release time | Previous issue |
| 15 | Securing the Web with Cisco Web Security Appliance (SWSA) | leads4pass | Nov 01, 2022 | 300-725 dumps questions 1-15 |
New Question 16:
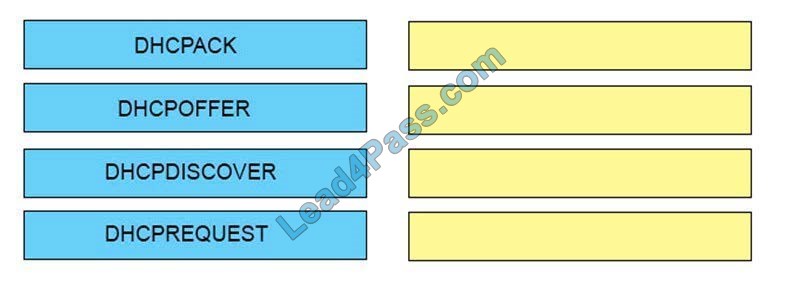
What causes authentication failures on a Cisco WSA when LDAP is used for authentication?
A. when the passphrase contains only 5 characters
B. when the passphrase contains characters that are not 7-bit ASCI
C. when the passphrase contains one of the following characters `@ # $ % ^\’
D. when the passphrase contains 50 characters
Correct Answer: B
New Question 17:

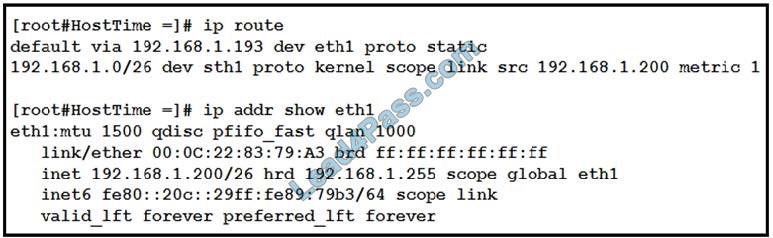
Refer to the exhibit. Which statement about the transaction log is true?
A. The log does not have a date and time
B. The proxy had the content and did not contact other servers
C. The transaction used TCP destination port 8187
D. The AnalizeSuspectTraffic policy group was applied to the transaction
Correct Answer: D
New Question 18:
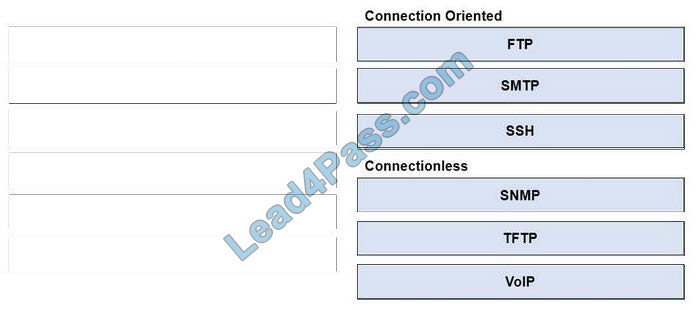
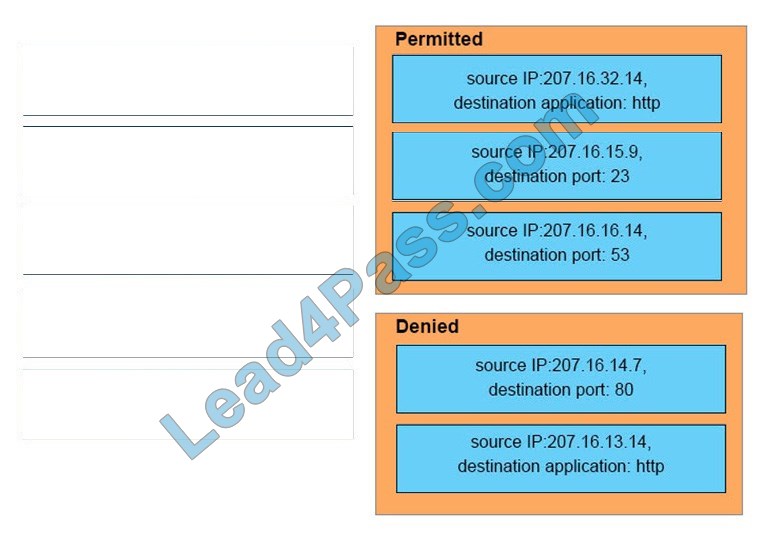
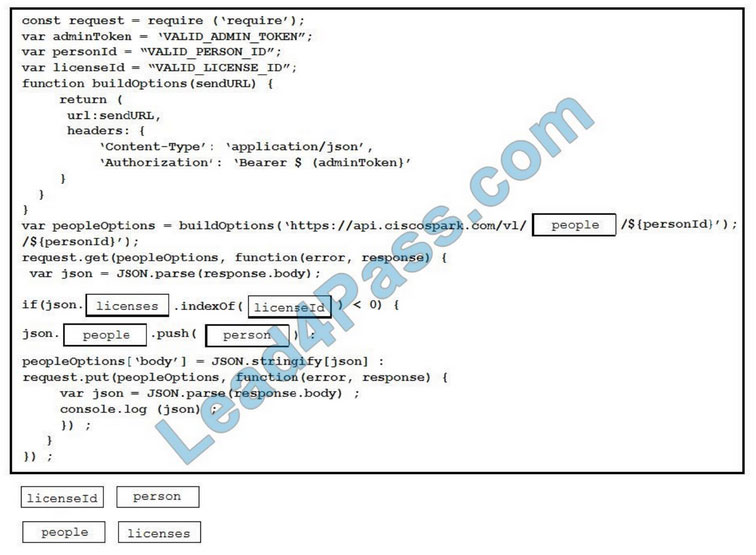
Which two features can be used with an upstream and downstream Cisco WSA web proxy to have the upstream WSA identify users by their client IP address? (Choose two.)
A. X-Forwarded-For
B. high availability
C. web cache
D. via
E. IP spoofing
Correct Answer: AD
New Question 19:
Which information in the HTTP request is used to determine if it is subject to the referrer exceptions feature in the Cisco WSA?
A. protocol
B. version
C. header
D. payload
Correct Answer: C
Requests for embedded content usually include the address of the site from which the request originated (this is known as the “referer” field in the request\’s HTTP header). This header information is used to determine the categorization of the referred content.
New Question 20:
Which key is needed to pair a Cisco WSA and Cisco ScanCenter for CTA?
A. public SSH key that the Cisco WSA generates
B. public SSH key that Cisco ScanCenter generates
C. private SSH key that Cisco ScanCenter generates
D. private SSH key that the Cisco WSA generates
Correct Answer: A
New Question 21:
Which behavior is seen while the policy trace tool is used to troubleshoot a Cisco WSA?
A. External DLP policies are evaluated by the tool
B. A real client request is processed and a EUN page is displayed
C. SOCKS policies are evaluated by the tool
D. The web proxy does not record the policy trace test requests in the access log when the tool is in use
Correct Answer: D
New Question 22:
What are all of the available options for configuring an exception to blocking for referred content?
A. all embedded/referred and all embedded/referred except
B. selected embedded/referred except, all embedded/referred, and selected embedded/referred
C. selected embedded/referred and all embedded/referred except
D. all embedded/referred, selected embedded/referred, and all embedded/referred except
Correct Answer: D
Reference: https://www.cisco.com/c/en/us/td/docs/security/wsa/wsa11-7/user_guide/b_WSA_UserGuide_11_7/b_WSA_UserGuide_11_7_chapter_01001.html (procedure)
New Question 23:
Which two parameters are mandatory to control access to websites with proxy authentication on a Cisco WSA? (Choose two.)
A. External Authentication
B. Identity-Enabled Authentication
C. Transparent User Identification
D. Credential Encryption
E. Authentication Realm
Correct Answer: DE
New Question 24:
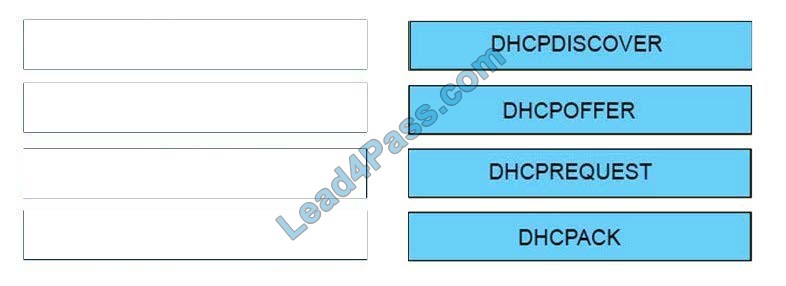
Which configuration option is suitable for explicit mode deployment?
A. PAC
B. WCCP
C. ITD
D. PBR
Correct Answer: A
In explicit-mode deployment, users will point the proxy setting to WSA. This can be done by pointing directly to WSA or via a PAC (Proxy Auto-Config) file.
New Question 25:
Which two sources provide data to Cisco Advanced Web Security Reporting to create dashboards? (Choose two.)
A. Cisco WSA devices
B. Cisco ISE
C. Cisco ASAv
D. Cisco Security MARS
E. Cisco Cloud Web Security gateways
Correct Answer: AE
New Question 26:
Which statement about Cisco Advanced Web Security Reporting integration is true?
A. AWSR uses IP addresses to differentiate Cisco WSA deployments
B. AWSR does not require a license to index data
C. AWSR can remove log files after they are indexed
D. AWSR installation is CLI-based on Windows and Red Hat Linux systems
Correct Answer: D
New Question 27:
Which two types of reports are scheduled on the Cisco WSA to analyze traffic? (Choose two.)
A. Layer 3 traffic monitor
B. URL categories
C. host statistics
D. application visibility
E. system capacity
Correct Answer: AD
Reference: https://www.cisco.com/c/en/us/td/docs/security/wsa/wsa11-0/user_guide/b_WSA_UserGuide/b_WSA_UserGuide_chapter_010101.pdf (8)
New Question 28:
Which two caches must be cleared on a Cisco WSA to resolve an issue in processing requests? (Choose two.)
A. authentication cache
B. application cache
C. logging cache
D. DNS cache
E. HTTP cache
Correct Answer: AD
New Question 29:
Which statement about configuring an identification profile for machine authentication is true?
A. Cloud Web Security Connector mode with an active directory enabled supports machine authentication
B. Identification profile machine ID is supported locally, but the Cisco WSA does not support machine ID authentication
C. Cloud Web Security with Kerberos enabled supports machine authentication
D. If an Active Directory realm is used, identification can be performed for an authenticated user or IP address but not for a machine ID
Correct Answer: C
New Question 30:
Which two benefits does AMP provide compared to the other scanning engines on the Cisco WSA? (Choose two.)
A. protection against malware
B. protection against zero-day attacks
C. protection against spam
D. protection against viruses
E. protection against targeted file-based attacks
Correct Answer: BD
…
leads4pass updates CCNP Security 300-725 exam questions and answers throughout the year and frequently shares a selection of free exam questions and answers, as shown above, candidates can improve themselves through online learning.
Also able to download the latest 300-725 dumps: https://www.leads4pass.com/300-725.html (Dumps PDF+VCE) to help them successfully pass the 300-725 Securing the Web with Cisco Web Security Appliance (SWSA) certification exam on their first attempt.