[New Microsoft Exam Dumps] Microsoft MCSA: Windows 10 70-697 Dumps Exam Questions And Answers Update
High quality Microsoft MCSA: Windows 10 70-697 dumps exam pdf files and vce youtube demo. Get the best uesful Microsoft MCSA: Windows 10 70-697 dumps exam questions and answers free download from leads4pass. “Configuring Windows Devices” is the name of Microsoft MCSE https://www.leads4pass.com/70-463.html exam dumps which covers all the knowledge points of the real Microsoft exam.
The best and most updated Microsoft MCSA: Windows 10 70-697 dumps exam practice resources and study guides free shared. Latest Microsoft MCSA: Windows 10 70-697 dumps pdf training materials update free try, pass Microsoft 70-697 exam test easily at the first time.
Download free latest Microsoft 70-696 dumps pdf files: https://drive.google.com/open?id=0B_7qiYkH83VRU3NnY0p0MHljbDg
Download free latest Microsoft 70-698 dumps pdf files: https://drive.google.com/open?id=0B_7qiYkH83VRVmd3UGtOOXgyR2M

QUESTION 1
You are an lT consultant for small and mid-sized business.
One of your clients wants to start using Virtual Smart Cards on its Windows 10 Enterprise laptops and tablets. Before implementing any changes, the client wants to ensure that the laptops and tablets support Virtual Smart Cards. You need to verify that the client laptops and tablets support Virtual Smart Cards.
What should you do?
A. Ensure that each laptop and tablet has a Trusted Platform Module (TPM) chip of version l.2 or greater.
B. Ensure that Bitlocker Drive Encryption is enabled on a system drive of the laptops and tablets.
C. Ensure that each laptop and tablet can read a physical smart card.
D. Ensure that the laptops and tablets are running Windows 10 Enter prise edition.
Correct Answer: A
QUESTION 2
Your network contains an Active Directory domain named contoso.com. Contoso.com is synchronized to a Microsoft Azure Active Directory. You have a Microsoft lntune subscription. Your company pLANs to implement a Bring Your Own Device (BYOD) policy. You will provide users with access to corporate data from their personal iOS devices.
You need to ensure that you can manage the personal iOS devices.
What should you do first?
A. lnstall the Company Portal app from the App1e App Store.
B. Create a device enrollment manager account.
C. Set a DNS alias for the enrollment server address.
D. Configure the lntune Service to Service Connector for Hosted Exchange.
E. Enroll for an App1e Push Notification (APN) certificate.
Correct Answer: E
QUESTION 3
You manage Microsoft lntune for a company named Contoso.lntune client computers run Windows 10 Enterprise.
You notice that there are 25 mandatory updates listed in the lntune administration console. You need to prevent users from receiving prompts to restart Windows following the installation of mandatory updates.
Which policy template should you use?
A. Microsoft lntune Agent Settings
B. Windows Configuration Policy
C. Microsoft lntune Center Settings
D. WindowsCustomPolicy(Windows 10andWindows 10Mobile)
Correct Answer: A
QUESTION 4
You have an Active Directory domain named contoso.com that contains a deployment of Microsoft System Center 20l2 Configuration Manager Service Pack 1 (SP1). 70-697 dumps You have a Microsoft lntune subscription that is synchronized to contoso.com by using the Microsoft Azure Active Directory Synchronization Tool (DirSync.) You need to ensure that you can use Configuration Manager to manage the devices that are registered to your Microsoft lntune subscription.
Which two actions should you perform? Each correct answer presents a part of the solution.
A. ln Microsoft lntune, create a new device enrollment manager account.
B. lnstall and configure Azure Active Directory Synchronization Services (AAD Sync.)
C. ln Microsoft lntune, configure an Exchange Connector.
D. ln Configuration Manager, configure the Microsoft lntune Connector role.
E. ln Configuration Manager, create the Microsoft lntune subscription.
Correct Answer: DE
QUESTION 5
You have a Microsoft lntune subscription.
You have three security groups named Security1, Security2 and Security3. Security1 is the parent group of Security2.
Security2 has l00 users.
You need to change the parent group of Security2 to be Security3.
What should you do first?
A. Edit the properties of Security1.
B. Edit the properties of Security2.
C. Delete security2.
D. Remove all users from Security2.
Correct Answer: C
QUESTION 6
You have a Windows 10 Enterprise computer named Computer1 that has the Hyper-V feature installed.
Computer1 hosts a virtual machine named VM1. VM1 runs Windows 10 Enterprise. VM1 connects to a private virtual network switch.
From Computer1, you need to remotely execute Windows PowerShell cmdlets on VM1.
What should you do?
A. Run the winrm.exe command and specify the -s parameter.
B. Run the Powershell.exe command and specify the -Command parameter.
C. Run the Receive-PSSession cmdlet and specify the -Name parameter.
D. Run the lnvoke-Command cmdlet and specify the -VMName parameter.
Correct Answer: D
QUESTION 7
HOTSPOT
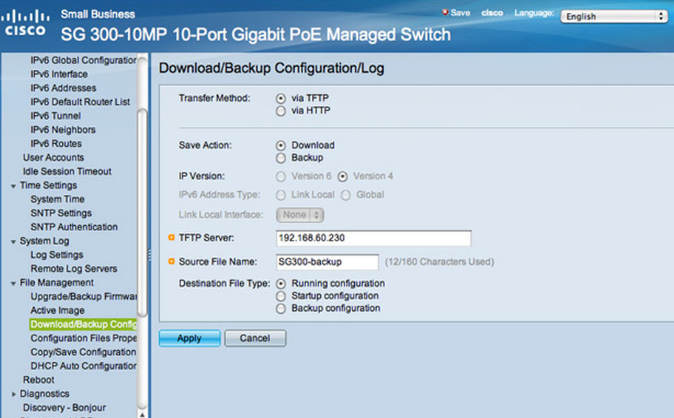
You have an Active Directory domain named contoso.com. You have a server that runs Windows Server 20l2 R2 and that is a Remote Desktop server
The RD Web Access Web App1ication settings are shown in the following graphic.
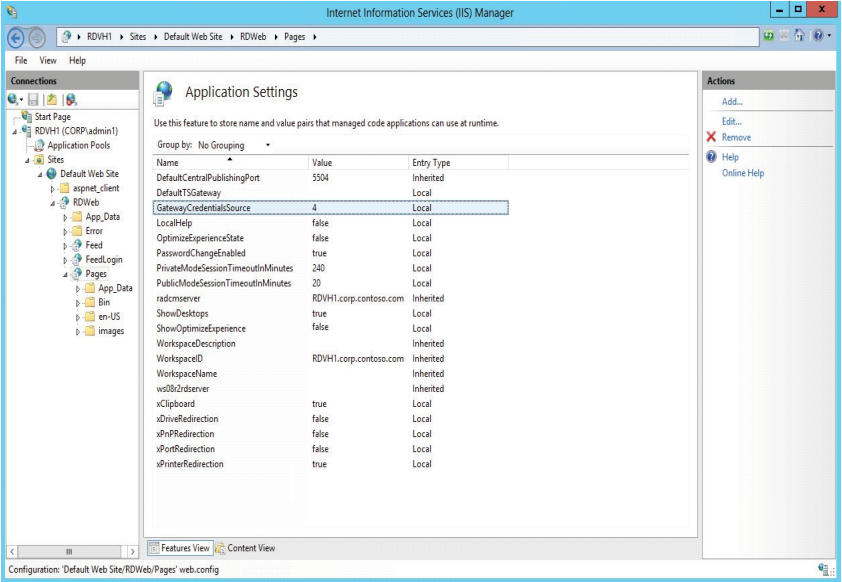
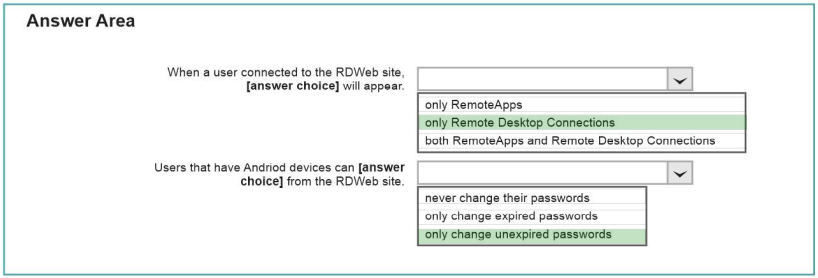
\Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. 70-697 dumps
NOTE: Each correct selection is worth one point.
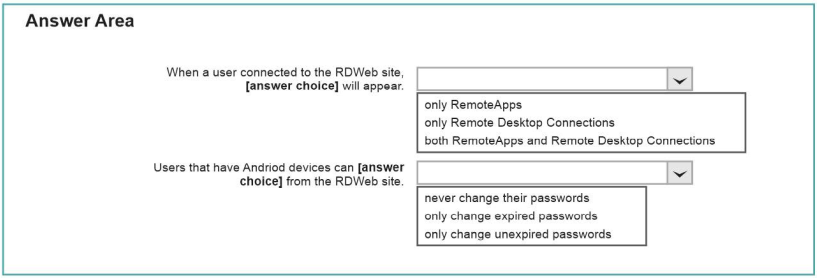
Correct Answer:
QUESTION 8
You are the desktop administrator for a small company.
Your work group environment consists of Windows 10 Enterprise computers. You want to prevent l0 help desk computers from sleeping. However, you want the screens to shut off after a certain period of time if the computers are not being used.
You need to configure and App1y a standard power configuration scheme for the l0 help desk computers on your network.
Which two actions should you perform? Each correct answer presents part of the solution.
A. lmport the power scheme by using POWERCFG /lMPORT on each of the remaining help desk computers. Set the power scheme to Active by using POWERCFG /S.
B. Use POWERCFG /X on one help desk computer to modify the power scheme to meet the requirements. Export the power scheme by using POWERCFG /EXPORT.
C. Use POWERCFG /S on one help desk computer to modify the power scheme to meet the requirements. Export the power scheme by using POWERCFG /EXPORT.
D. lmport the power scheme by using POWERCFG /lMPORT on each of the remaining help desk computers. Set the power scheme to Active by using POWERCFG /X.
Correct Answer: AB
]QUESTION 9
A company has an Active Directory Domain Services(ADDS) domain. All client computers run Windows 10 Enterprise.
Some computers have a Trusted Platform Module (TPM) chip.
You need to configure a single Group Policy object (GPO) that will allow Windows Bitlocker Drive Encryption on all client computers.
Which two actions should you perform? Each correct answer presents part of the solution.
A. Enable the Require additional authentication at startup policy setting.
B. Enable the Enforce drive encryption type on operating system drives policy setting.
C. Enable the option to allow Bitlocker without a compatible TPM.
D. Configure the TPM validation profile to enable Plat form Configuration Registerindices(PCRs)0,2,4,andll.
Correct Answer: AC
QUESTION 10
You deploy several tablet PCs that run Windows 10 Enterprise.
You need to minimize power usage when the user presses the sleep button.
What should you do? 70-697 dumps
A. ln Power Options, configure the sleep button setting to Sleep.
B. ln Power Options, configure the sleep button setting to Hibernate.
C. Configure the active power pLAN to set the system cooling policy to passive.
D. Disable the C-State control in the computer’s BlOS.
Correct Answer: B
QUESTION 11
Employees are permitted to bring personally owned portable Windows 10 Enterprise computers to the office. They are permitted to install corporate App1ications by using the management infrastructure agent and access corporate emailbyusing the Mailapp.
An employee’s personally owned portable computer is stolen.
You need to protect the corporate App1ications and email messages on the computer. Which two actions
should you perform? Each correct answer presents part of the solution.
A. Prevent the computer from connecting to the corporate wireless network.
B. Change the user’s password.
C. Disconnect the computer from the management infrastructure.
D. lnitiate a remote wipe.
Correct Answer: BD
QUESTION 12
You support Windows 10 Enterprise computers.
Your company has started testi g App1ication Virtualization (App-V) App1ications on several laptops. You discover that the App-V App1ications are available to users even when the laptops are offline. You need to ensure that the App-V App1ications are available to users only when they are connected to the company network.
What should you do?
A. Change user permissions to the App-V App1ications.
B. Disable the Disconnected operation mode.
C. Configure mandatory profiles for laptop users.
D. Reset the App-V client FileSystem cache.
Correct Answer: B
The best and most updated latest Microsoft MCSA: Windows 10 https://www.leads4pass.com/70-697.html dumps pdf training resources which are the best for clearing 70-697 exam test, and to get certified by Microsoft MCSA: Windows 10.