leads4pass continues to share the latest 15 DevNet Professional 300-915 DEVIOT exam questions and answers to help you study online, welcome to download the 300-915 dumps provided by leads4pass:https://www.leads4pass.com/300-915.html Contains 59 practical and valid exam questions and answers, and provides PDF files and VCE simulation tools to help you quickly learn and pass the DevNet Professional 300-915 DEVIOT exam.
| Number of exam questions | Exam name | From | Release time | Previous issue |
| 15 | Developing Solutions using Cisco IoT and Edge Platforms (DEVIOT) | leads4pass | Oct 10, 2022 | 300-915 exam dumps questions (Q1-Q15) |
Continue your DevNet Professional 300-915 DEVIOT exam knowledge:
New Question 16:
Which two states are applications expected to be seen in when they are managed on Cisco IOx? (Choose two.)
A. DEACTIVATED
B. ACTIVATED
C. ALLOWED
D. STOPPED
E. VALIDATED
Correct Answer: BD
New Question 17:
When an RS232 device is connected to a Cisco IR829 router, the data collected is not being parsed correctly by the edge application.
Which two steps should be taken to troubleshoot the issue? (Choose two.)
A. SSH access on the Cisco IR829 router must be enabled for IOx Guest OS.
B. Communication mode must be set to half duplex over a serial connection.
C. Serial cable length should not exceed 1.5 meters.
D. Ensure that communication parameters like baud rate and parity are set correctly.
E. Set the cable connections based on the PIN layout from the sensor vendor.
Correct Answer: DE
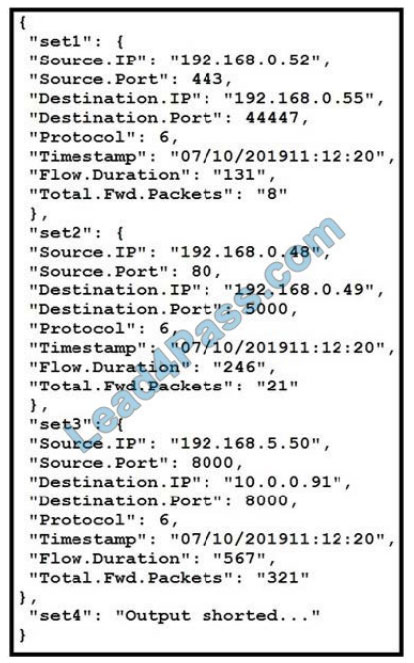
New Question 18:
Refer to the exhibit. Which two statements about MQTT messaging are true? (Choose two.)
A. Result in code 5 means the connection is accepted; result code 0 means the connection is “refused, not authorized”.
B. Redundant ClientIDs are supported by MQTT brokers.
C. MQTT does not support a “keep alive” functionality because it runs on top of TCP.
D. Result code 0 means the connection is accepted; result code 5 means the connection is “refused, not authorized”.
E. Brokers can send the Last Will and Testament messages on behalf of the client.
Correct Answer: DE
New Question 19:
How do the Cisco router (IR) and switch (IE) portfolios support edge data services?
A. Edge data services can be run and managed as containers using Cisco IOx.
B. Edge data services can run only in virtual machines on a separate compute layer.
C. Edge data services are aliases for IR/IE configuration services.
D. Edge data services run as separate instances only on virtual machines.
Correct Answer: C
New Question 20:
Refer to the exhibit. While troubleshooting an error on an application descriptor for a Docker app in Cisco IOx (package.YAML), the app type appears to be missing. Which app type must be added to the snippet to resolve the issue?
A. paas
B. docker-vm
C. docker
D. docker-app
Correct Answer: C
New Question 21:
Refer to the exhibit. Which two statements about data flow are true? (Choose two.)
A. Another AMQP broker should be implemented on the customer cloud.
B. Instead of AMQP, MQTT should be used for compatibility issues in a cloud-to-cloud connection.
C. A VPN tunnel is not necessary because the MQTT payload is encrypted by default.
D. The gateway must stay constantly connected to the Kinetic cloud to avoid blank data sets, even when using caching functions.
E. The Python application could use the paho-mqtt library.
Correct Answer: BE
New Question 22:
Which two statements define the mechanism for console access of the Guest Operating System from the Cisco IR829 router? (Choose two.)
A. The Guest OS can be accessed by default on Telnet port 2070 from the Cisco IR829 console.
B. The Guest OS console is available directly by the AUX port 3362 from the Cisco IR829 router.
C. The Guest OS can be accessed directly using the console port on the Cisco IR829 router.
D. The Guest OS can be accessed by initiating SSH from the Cisco IR829 console.
E. The Guest OS console is available only when a static IP is configured on the host.
Correct Answer: AD
New Question 23:
The environment for an Industrial IoT project in a large open pit mine is being scoped. The location has a large amount of dust and the device will be exposed to less than 1 meter of water temporarily.
When the edge device is being chosen, which Ingress protection rating must be used?
A. IP37
B. IP61
C. IP67
D. IP76
Correct Answer: C
New Question 24:
Which two statements about how to provision and manage data originators in a cloud environment are true? (Choose two.)
A. The provisioning of digital identities is the responsibility of the data originators.
B. Cloud providers offer services for automated device provisioning, which allows the lifecycle of the cloud representation for data originators to be managed.
C. Cloud providers offer application programming interfaces, which allow a programmatic provisioning of data originators.
D. There is no need to provision and manage access for data originators in the cloud.
E. access to public clouds must be configured and managed manually.
Correct Answer: CE
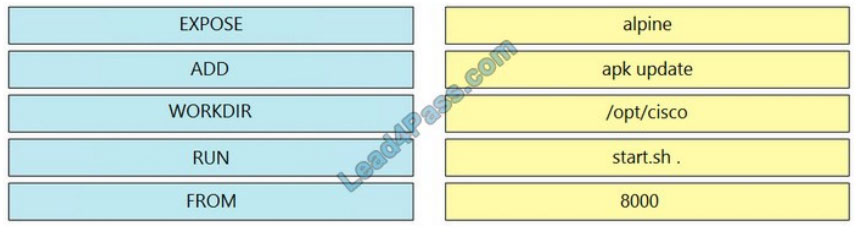
New Question 25:
Refer to the exhibit. Which line of code completes the Dockerfile?
A. RUN chmod 777 /usr/bin/sample.py
B. RUN chown root:root /usr/bin/sample.py
C. WORKDIR /usr/bin
D. USER root
Correct Answer: A
New Question 26:
As part of an IoT project, an organization is developing an application that will share multiple clients using a REST API.
Based on the software development process, what are two valid technical activities that can be suggested to secure the REST API that is developed during the development of the software? (Choose two.)
A. Respond to request failures in detail to allow users for easier troubleshoot.
B. Implement HTTP whitelisting to only methods that are allowed.
C. Implement and review audit logs for security-related events.
D. Reject HTTP methods that are invalid with an error code 404.
E. Implement physical firewalling and access control to the resources.
Correct Answer: BD
New Question 27:
Which two actions must be completed before starting the process of sending IoT data to the cloud via edge routers? (Choose two.)
A. Measure the voltage, power rating, and quiescent current for the sensors that send data to the cloud.
B. Gather the hardware (MAC) addresses of local and cloud routers to ensure low-latency communication.
C. Collect information about the CPU architecture in the cloud and edge to ensure that they match.
D. Gather the interval, the volume, and the latency that the data must be provisioned with.
E. Collect information about growth, required elasticity, and high availability of the provisioning process.
Correct Answer: DE
New Question 28:
After an application is deployed, potential issues arise around connectivity. As part of the troubleshooting process, the IP address must be determined to ensure end-to-end communication.
Which method provides the required details using the Cisco IOx CLI?
A. ioxclient application status
B. ioxclient application metrics
C. ioxclient application getconfig
D. ioxclient application info
Correct Answer: D
New Question 29:
Where are edge data services typically instantiated?
A. at the edge of the network
B. in the cloud
C. in the data center
D. in a private cloud
Correct Answer: A
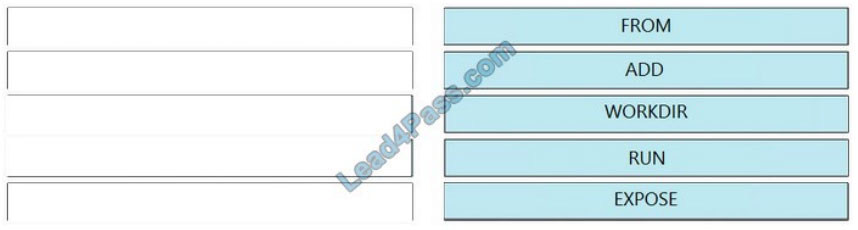
New Question 30:
Refer to the exhibit. A new application has just been developed as a Docker container. What is the missing step for packaging the container ready for deployment in IOx?
A. Pull/push the image to the Docker registry.
B. Build the package.YAML files.
C. Build the package. cert file to sign the app.
D. Log in to the device manager and load the application.
Correct Answer: B
…
Get 59 real and up-to-date DevNet Professional 300-915 DEVIOT exam questions Check out this link to help you pass the exam 100%.
BTW, DOWNLOAD part of leads4pass 300-915 dumps from Google Drive:https://drive.google.com/file/d/1PSiCxtGU6gJDUSNO-wb9h0jlVetNDrpq/