
Cisco CyberOps Professional exam series include (300-215 CBRFIR, 350-201 CBRCOR).
These are popular exams. Passing any exam will improve your career path.
Cisco CyberOps Professional exam series learning experience:
step 1: you definitely need to know Cisco’s official information and exam details>> https://www.cisco.com/c/en/us/training-events/training-certifications/exams/current-list/300-215-cbrfir.html
In the official information, you will get: exam overview, related certifications, Cisco official training, frequently asked questions, and schedule exams
Step 2: You should get the latest free Cisco exam practice questions>> https://www.vcecert.com/category/real-cisco-exam-questions-and-answers-online-exam-certifications/cisco-cyberops-professional/
Here are the questions and answers of the Cisco CyberOps Professional exam series shared by leads4pass for free
Step 3: Pass the exam secrets and get the latest updated Cisco CyberOps Professional exam dumps>> https://www.leads4pass.com/cyberops-professional.html
The Cisco CyberOps Professional exam series includes 300-215 and 350-201 exam items. Include PDF and VCE in leads4pass to help you successfully pass the exam
Here: Share free Cisco 300-215 exam practice questions
Exam answers are available at the end of the article. You can also skip this stage and get the complete 300-215 exam dumps directly https://www.leads4pass.com/300-215.html
QUESTION 1
What is the goal of an incident response plan?
A. to identify critical systems and resources in an organization
B. to ensure systems are in place to prevent an attack
C. to determine security weaknesses and recommend solutions
D. to contain an attack and prevent it from spreading
Reference: https://www.forcepoint.com/cyber-edu/incident-response
QUESTION 2
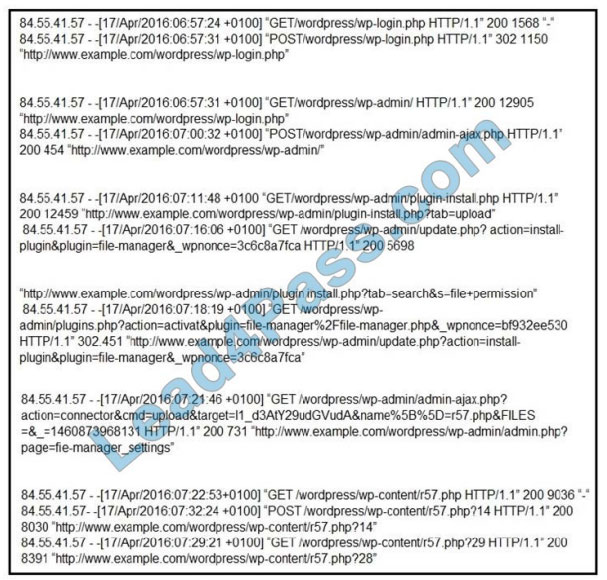
Refer to the exhibit. Which two determinations should be made about the attack from the Apache access logs? (Choose two.)
A. The attacker used r57 exploit to elevate their privilege.
B. The attacker uploaded the word press file manager trojan.
C. The attacker performed a brute force attack against word press and used SQL injection against the backend
database.
D. The attacker used the word press file manager plugin to upload r57.php.
E. The attacker logged on normally to word press admin page.
QUESTION 3
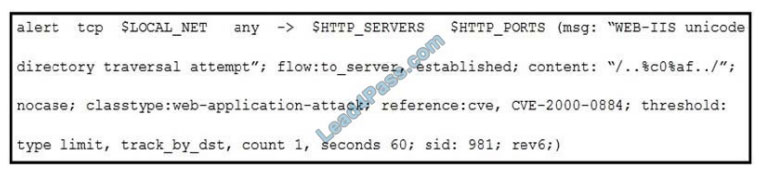
Refer to the exhibit. A company that uses only the Unix platform implemented an intrusion detection system. After the
initial configuration, the number of alerts is overwhelming, and an engineer needs to analyze and classify the alerts. The highest number of alerts were generated from the signature shown in the exhibit. Which classification should the
engineer assign to this event?
A. True Negative alert
B. False Negative alert
C. False Positive alert
D. True Positive alert
QUESTION 4
A threat actor attempts to avoid detection by turning data into a code that shifts numbers to the right four times. Which anti-forensics technique is being used?
A. encryption
B. tunneling
C. obfuscation
D. poisoning
Reference: https://www.vadesecure.com/en/malware-analysis-understanding-code-obfuscationtechniques/#:~:text=Obfuscation%20of%20character%20strings%20is,data%20when%20the%20code%20executes.
QUESTION 5
DRAG-DROP
Drag and drop the capabilities on the left onto the Cisco security solutions on the right.
Select and Place:
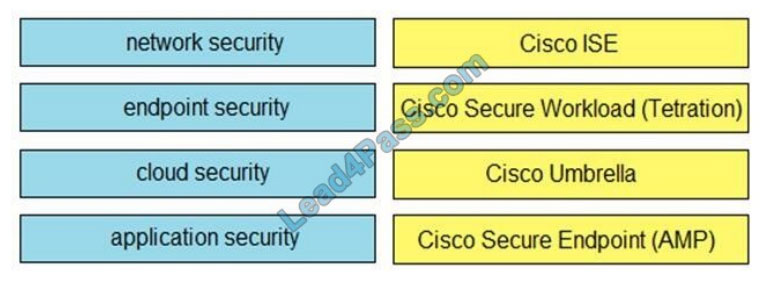
Correct Answer:
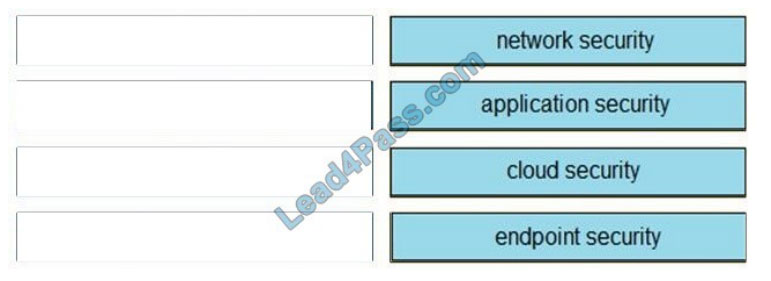
QUESTION 6
An engineer is investigating a ticket from the accounting department in which a user discovered an unexpected
application on their workstation. Several alerts are seen from the intrusion detection system of unknown outgoing
internet traffic from this workstation. The engineer also notices a degraded processing capability, which complicates the analysis process. Which two actions should the engineer take? (Choose two.)
A. Restore to a system recovery point.
B. Replace the faulty CPU.
C. Disconnect from the network.
D. Format the workstation drives.
E. Take an image of the workstation.
QUESTION 7
An incident response team is recommending changes after analyzing a recent compromise in which:
a large number of events and logs were involved;
team members were not able to identify the anomalous behavior and escalate it in a timely manner;
several network systems were affected as a result of the latency in detection;
security engineers were able to mitigate the threat and bring systems back to a stable state; and
the issue reoccurred shortly after and systems became unstable again because the correct information was not
gathered during the initial identification phase.
Which two recommendations should be made for improving the incident response process? (Choose two.)
A. Formalize reporting requirements and responsibilities to update management and internal stakeholders throughout
the incident-handling process effectively.
B. Improve the mitigation phase to ensure causes can be quickly identified, and systems returned to a functioning state.
C. Implement an automated operation to pull systems events/logs and bring them into an organizational context.
D. Allocate additional resources for the containment phase to stabilize systems in a timely manner and reduce an
attack\’s breadth.
E. Modify the incident handling playbook and checklist to ensure alignment and agreement on roles, responsibilities,
and steps before an incident occurs.
QUESTION 8
A network host is infected with malware by an attacker who uses the host to make calls for files and shuttle traffic to
bots. This attack went undetected and resulted in a significant loss. The organization wants to ensure this does not
happen in the future and needs a security solution that will generate alerts when command and control communication from an infected device is detected. Which network security solution should be recommended?
A. Cisco Secure Firewall ASA
B. Cisco Secure Firewall Threat Defense (Firepower)
C. Cisco Secure Email Gateway (ESA)
D. Cisco Secure Web Appliance (WSA)
QUESTION 9
An attacker embedded a macro within a word processing file opened by a user in an organization\’s legal department.
The attacker used this technique to gain access to confidential financial data. Which two recommendations should a
security expert make to mitigate this type of attack? (Choose two.)
A. controlled folder access
B. removable device restrictions
C. signed macro requirements
D. firewall rules creation
E. network access control
QUESTION 10
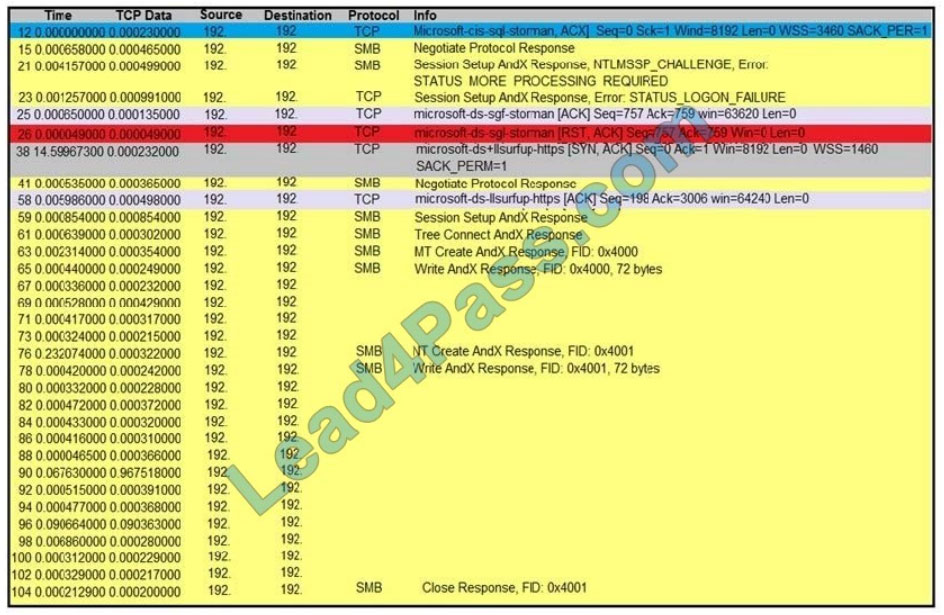
Refer to the exhibit. An engineer is analyzing a TCP stream in a Wireshark after a suspicious email with a URL. What
should be determined about the SMB traffic from this stream?
A. It is redirecting to a malicious phishing website,
B. It is exploiting redirect vulnerability
C. It is requesting authentication on the user site
D. It is sharing access to files and printers.
QUESTION 11
Over the last year, an organization\’s HR department has accessed data from its legal department on the last day of
each month to create a monthly activity report. An engineer is analyzing suspicious activity alerted by a threat
intelligence platform that an authorized user in the HR department has accessed legal data daily for the last week. The
engineer pulled the network data from the legal department\’s shared folders and discovered above average-size data
dumps. Which threat actor is implied from these artifacts?
A. privilege escalation
B. internal user errors
C. malicious insider
D. external exfiltration
QUESTION 12
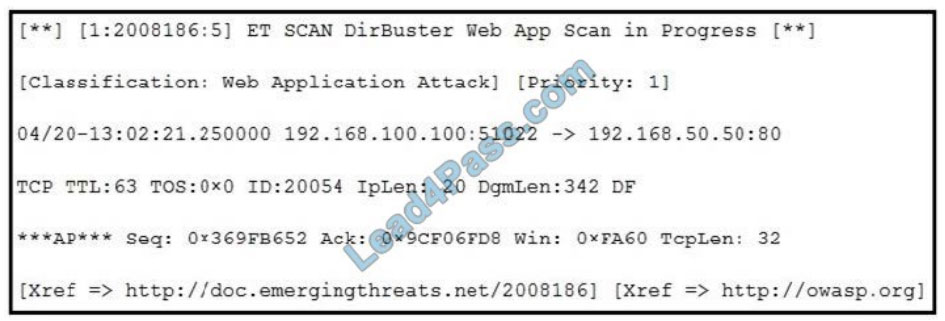
Refer to the exhibit. According to the SNORT alert, what is the attacker performing?
A. brute-force attack against the web application user accounts
B. XSS attack against the target webserver
C. brute-force attack against directories and files on the target webserver
D. SQL injection attack against the target webserver
QUESTION 13
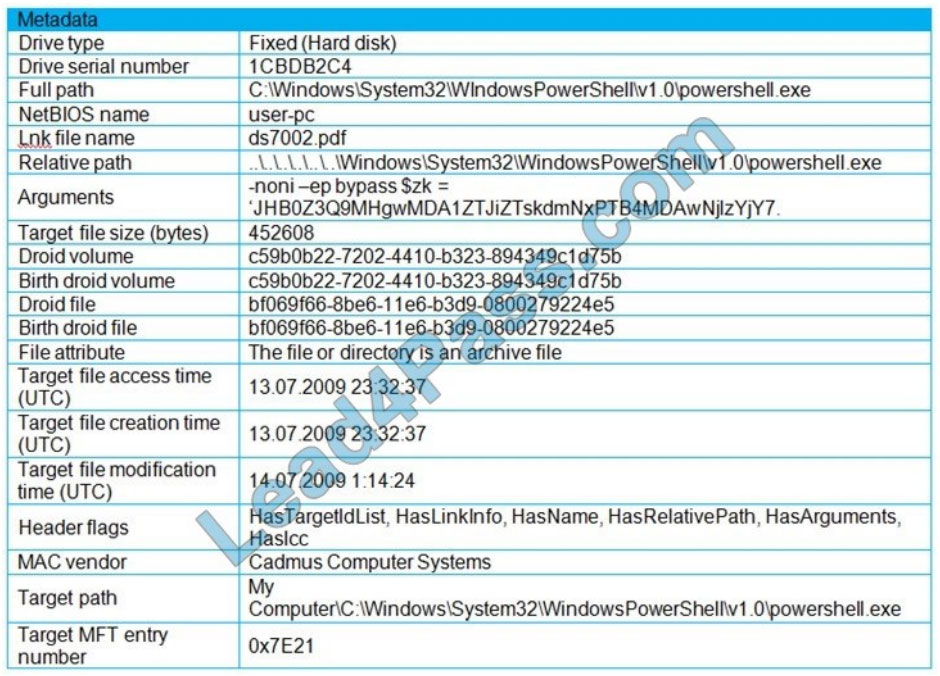
Refer to the exhibit. An engineer is analyzing a . LNK (shortcut) file recently received as an email attachment and
blocked by email security as suspicious. What is the next step an engineer should take?
A. Delete the suspicious email with the attachment as the file is a shortcut extension and does not represent any threat.
B. Upload the file to a virus checking engine to compare with well-known viruses as the file is a virus disguised as a
legitimate extension.
C. Quarantine the file within the endpoint antivirus solution as the file is ransomware which will encrypt the documents
of a victim.
D. Open the file in a sandbox environment for further behavioral analysis as the file contains a malicious script that runs on execution.
QUESTION 14
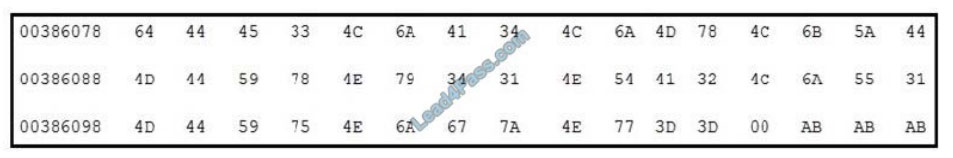
Refer to the exhibit. Which encoding technique is represented by this HEX string?
A. Unicode
B. Binary
C. Base64
D. Charcode
Reference: https://www.suse.com/c/making-sense-hexdump/
QUESTION 15

Refer to the exhibit. Which two actions should be taken as a result of this information? (Choose two.)
A. Update the AV to block any file with hash “cf2b3ad32a8a4cfb05e9dfc45875bd70”.
B. Block all emails sent from an @state.gov address.
C. Block all emails with pdf attachments.
D. Block emails sent from [email protected] with an attached pdf file with md5 hash
“cf2b3ad32a8a4cfb05e9dfc45875bd70”.
E. Block all emails with subject containing “cf2b3ad32a8a4cfb05e9dfc45875bd70”.
Publish the answer:
| Q1 | Q2 | Q3 | Q4 | Q5 | Q6 | Q7 | Q8 | Q9 | Q10 | Q11 | Q12 | Q13 | Q14 | Q15 |
| D | CD | C | C | image | AE | CE | B | AC | B | C | C | D | B | AB |
Cisco 300-215 exam PDF share for free on google drive
In order to facilitate the study habits of more people, here is a part of the latest 300-215 exam PDF from leads4pass 300-215 dumps
The Cisco CyberOps Professional contains a wealth of exam content. The whole series contains 2 types of test words.
Passing the exam is really not an easy task. In leads4pass, you can get a dumps of the exam to help you pass the exam easily.
The free Cisco 300-215 exam practice questions shared above are only part of the complete dumps. For a complete Cisco 300-215 dumps, Click to enter the https://www.leads4pass.com/300-215.html dumps page.




