
Candidates can use New update CyberOps Associate 200-201 dumps with PDF and VCE: https://www.leads4pass.com/200-201.html (406 Q&A), successfully passed Threat Hunting and Defending using Cisco Technologies for CyberOps (CBROPS) exam.
New update 200-201 dumps actually cover all the exam content of the complete CyberOps Associate: Security concepts, Security monitoring, Host-based analysis, Network intrusion analysis, and Security policies and procedures.
Download the free CyberOps Associate 200-201 (2025) PDF:https://drive.google.com/file/d/1_7bAIxujf7ExqOcYeP1OxcVhanvGKFG2/view?usp=sharing
2025 Tips:
Coming this January: Cisco’s CyberOps certifications will be updated to Cisco Cybersecurity certifications.
Effective January 21, 2025 our CyberOps certifications will be updated to Cisco Cybersecurity certifications and will include new AI-related exam topics. With the help of predictive AI in the Cybersecurity Associate and AI-powered and AI-driven analysis in Cybersecurity Professional certifications, you can prepare yourself for the latest in AI-driven Cybersecurity trends and job roles.
The CyberOps Associate exam 200-201 CBROPS v1.1 is being updated to v1.2.
- Last date to test for 200-201 CBROPS v1.1 is January 20, 2025.
- First date to test for 200-201 CBROPS v1.2 is January 21, 2025.
- To see or download the CBROPS 1.2 exam topics, click here
2025 CyberOps Associate 200-201 exam questions and answers online:
| Number of exam questions | Exam name | From | Release time | Previous issue |
| 15 | Threat Hunting and Defending using Cisco Technologies for CyberOps (CBROPS) | leads4pass | Dec 31, 2024 | 200-201 dumps exam questions |
New Question 1:
What is a benefit of using asymmetric cryptography?
A. decrypts data with one key
B. fast data transfer
C. secure data transfer
D. encrypts data with one key
Correct Answer: C
New Question 2:
What are two social engineering techniques? (Choose two.)
A. privilege escalation
B. DDoS attack
C. phishing
D. man-in-the-middle
E. pharming
Correct Answer: CE
New Question 3:
Which action matches the weaponization step of the Cyber Kill Chain Model?
A. Develop a specific malware to exploit a vulnerable server.
B. Construct a trojan and deliver it to the victim.
C. Match a known script to a vulnerability.
D. Scan open services and ports on a server.
Correct Answer: A
New Question 4:
A SOC analyst is investigating an incident that involves a Linux system that is identifying specific sessions. Which identifier tracks an active program?
A. application identification number
B. active process identification number
C. runtime identification number
D. process identification number
Correct Answer: D
New Question 5:
What is a description of a man-in-the-middle network attack?
A. After attackers penetrate a network, they can use privilege escalation to expand their reach.
B. Attackers build botnets, large fleets of compromised devices, and use them to direct false traffic at networks or servers.
C. It involves attackers intercepting traffic, either between a network and external sites or within a network.
D. Attackers replicate malicious traffic as legitimate and bypass network protection solutions.
Correct Answer: C
New Question 6:
Which regex matches only on all lowercase letters?
A. [az]+
B. [^az]+
C. az+
D. a*z+
Correct Answer: A
New Question 7:
A security specialist notices 100 HTTP GET and POST requests for multiple pages on the web servers. The agent in the requests contains PHP code that, if executed, creates and writes to a new PHP file on the webserver. Which event category is described?
A. reconnaissance
B. action on objectives
C. installation
D. exploitation
Correct Answer: D
New Question 8:
What is the virtual address space for a Windows process?
A. physical location of an object in memory
B. set of pages that reside in the physical memory
C. system-level memory protection feature built into the operating system
D. set of virtual memory addresses that can be used
Correct Answer: D
New Question 9:
A malicious file has been identified in a sandbox analysis tool.
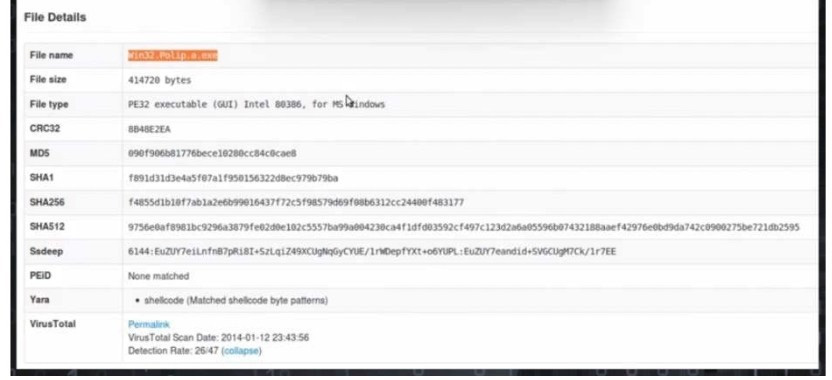
Which piece of information is needed to search for additional downloads of this file by other hosts?
A. file header type
B. file size
C. file name
D. file hash value
Correct Answer: D
New Question 10:
DRAG DROP
Drag and drop the definition from the left onto the phase on the right to classify intrusion events according to the Cyber Kill Chain model.
Select and Place:
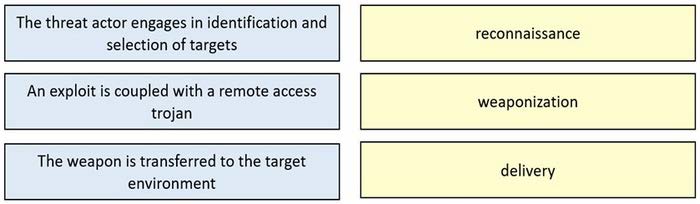
Correct Answer:

Delivery: This step involves transmitting the weapon to the target. Weaponization: In this step, the intruder creates a malware weapon like a virus, worm or such in order to exploit the vulnerabilities of the target. Depending on the target and the purpose of the attacker, this malware can exploit new, undetected vulnerabilities (also known as the zero-day exploits) or it can focus on a combination of different vulnerabilities. Reconnaissance: In this step, the attacker / intruder chooses their target. Then they conduct an in-depth research on this target to identify its vulnerabilities that can be exploited.
New Question 11:
An analyst discovers that a legitimate security alert has been dismissed. Which signature caused this impact on network traffic?
A. true negative
B. false negative
C. false positive
D. true positive
Correct Answer: B
A false negative occurs when the security system (usually a WAF) fails to identify a threat. It produces a “negative” outcome (meaning that no threat has been observed), even though a threat exists.
New Question 12:
What is the impact of false positive alerts on business compared to true positive?
A. True positives affect security as no alarm is raised when an attack has taken place, while false positives are alerts raised appropriately to detect and further mitigate them.
B. True-positive alerts are blocked by mistake as potential attacks, while False-positives are actual attacks Identified as harmless.
C. False-positive alerts are detected by confusion as potential attacks, while true positives are attack attempts identified appropriately.
D. False positives alerts are manually ignored signatures to avoid warnings that are already acknowledged, while true positives are warnings that are not yet acknowledged.
Correct Answer: C
New Question 13:
Which type of evasion technique is accomplished by separating the traffic into smaller segments before transmitting across the network?
A. encryption
B. tunneling
C. proxies
D. fragmentation
Correct Answer: D
New Question 14:
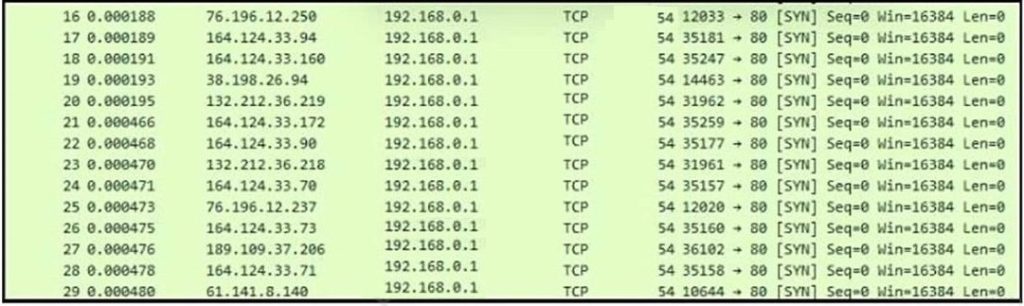
Refer to the exhibit. What is occurring?
A. ARP spoofing attack
B. man-in-the-middle attack
C. brute-force attack
D. denial-of-service attack
Correct Answer: D
New Question 15:
What does the SOC metric MTTC provide in incident analysis?
A. average time it takes to recognize and stop the incident
B. average time it takes to fix the issues caused by the incident
C. average time it takes to detect that the incident has occurred
D. average time the attacker has access to the environment
Correct Answer: A
…
Download the above CyberOps Associate 200-201 exam questions and answers (2025): https://drive.google.com/file/d/1_7bAIxujf7ExqOcYeP1OxcVhanvGKFG2/view?usp=sharing
New update CyberOps Associate 200-201 dumps have been verified to be real and effective, and 264 newly updated exam questions cover the complete 200-201 CBROPS certification exam. Candidates click here for the latest 200-201 dumps online to ensure they pass the 200-201 CBROPS Certification Exam.



