Latest Cisco CCNP Security 300-210 dumps pdf training resources and study guides download free try from leads4pass. Useful Cisco CCNP Security 300-210 dumps pdf files and vce youtube demo update free shared. “Implementing Cisco Threat Control Solutions (SITCS)” is the name of Cisco CCNP Security https://www.leads4pass.com/300-210.html exam dumps which covers all the knowledge points of the real Cisco exam. High quality Cisco CCNP Security 300-210 dumps exam questions and answers update free try, pass Cisco 300-210 exam test easily.
The best Cisco 300-210 dumps pdf training resources: https://drive.google.com/open?id=0B_7qiYkH83VRZElkNlhzd3h0elU
The best Cisco 300-175 dumps pdf training resources: https://drive.google.com/open?id=0B_7qiYkH83VRMjJsWXh1NTRUb28
New Cisco CCNP Security 300-210 Dumps Exam Questions & Answers (1-30)
QUESTION 1
An engineer wants to improve web traffic performance by proxy caching. Which technology provides this improvement?
A. Firepower
B. FireSIGT
C. WSA
D. ASA
Correct Answer: C
QUESTION 2
Which cloud-based malware detection engine uses machine-learning detection techniques in the Cisco Advanced Malware Protection cloud?
A. third-party detections
B. Spero
C. Ethos
D. Memcache
Correct Answer: B
QUESTION 3
which two options are the basic parts of a Snort rule? (Choose two)
A. rule policy
B. rule header
C. Rule assignment and ports
D. rule options
E. Rule footer
Correct Answer: BD
QUESTION 4
Which three statements about Cisco CWS are true’? (Choose three )
A. It provides protection against zero-day threats.
B. Cisco SIO provides it with threat updates in near real time.
C. It supports granular application policies.
D. Its Roaming User Protection feature protects the VPN from malware and data breaches.
E. It supports local content caching.
F. Its Cognitive Threat Analytics feature uses cloud-based analysis and detection to block threats outside the network.
Correct Answer: ABC
QUESTION 5
When creating an SSL policy on Cisco FirePOWER, which three options do you have
A. do not decrypt
B. trust
C. allow
D. block with reset
E. block
F. encrypt
Correct Answer: ADE
QUESTION 6
With Cisco FirePOWER Threat Defense software, which interface mode do you configure to passively receive traffic that passes the appliance?
A. transparent
B. routed
C. passive
D. inline set
E. inline tap
Correct Answer: C
QUESTION 7
Which two statement about Cisco Firepower file and intrusion inspection under control policies are true? 300-210 dumps (Choose two.)
A. File inspection occurs before intrusion prevention.
B. Intrusion Inspection occurs after traffic is blocked by file type.
C. File and intrusion drop the same packet.
D. Blocking by file type takes precedence over malware inspection and blocking
E. File inspection occurs after file discovery
Correct Answer: AE
QUESTION 8
Which Cisco FirePOWER setting is used to reduce the number of events received in a period of time and avoid being overwhelmed?
A. thresholding
B. rate-limiting
C. limiting
D. correlation
Correct Answer: D
QUESTION 9
Which Cisco Web Security Appliance feature enables the appliance to block suspicious traffic on all of its ports and IP addresses?
A. explicit forward mode
B. Layer 4 Traffic Monitor
C. transparent mode
D. Secure Web Proxy
Correct Answer: B
QUESTION 10
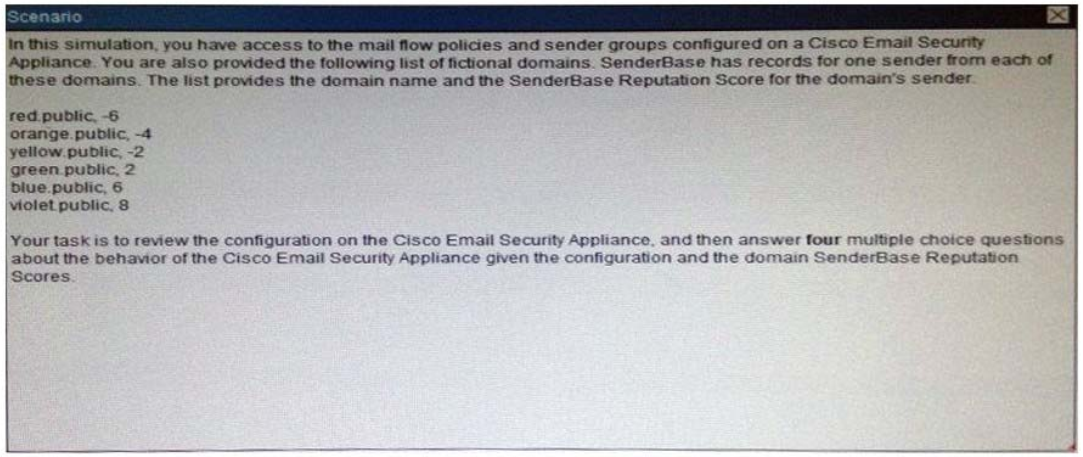
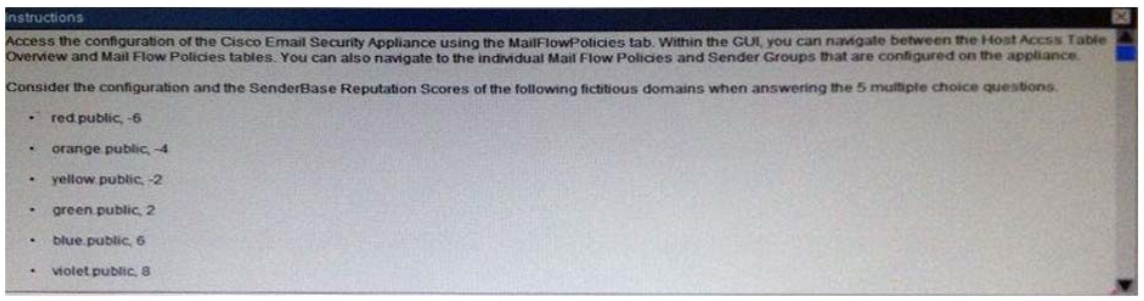

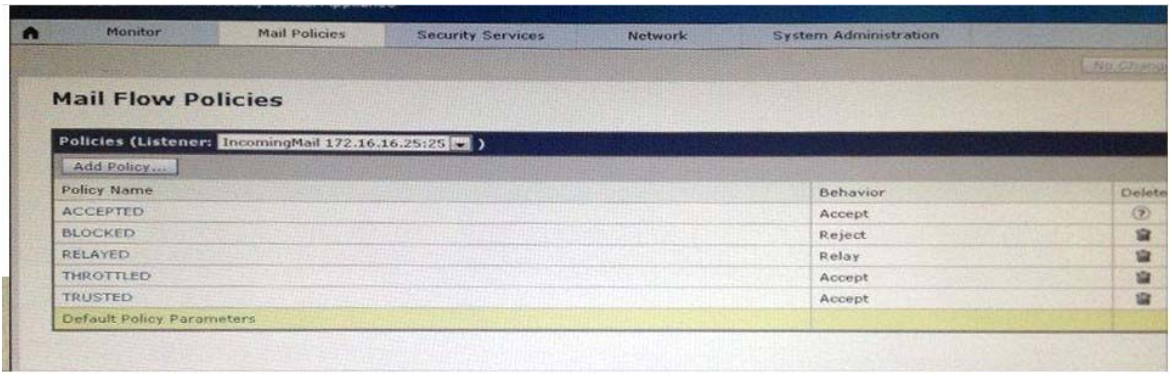
What is the maximum message size that the Cisco Email Security Appliance will accept from the violet.public domain?
A. 1 KB
B. 100 KB
C. 1 MB
D. 10 MB
E. 100 MB
F. Unlimited
Correct Answer: D
QUESTION 11
Which option is a benefit of Cisco Email Security virtual appliance over the Cisco ESA appliance?
A. global threat intelligence updates from Talos
B. reduced space and power requirements
C. outbound message protection
D. automated administration
Correct Answer: B
QUESTION 12
An engineer must architect an AMP private cloud deployment. What is the benefit of running in air-gaped mode?
A. Internet connection is not required for disposition.
B. Database sync time is reduced.
C. Disposition queries are done on AMP appliances.
D. A dedicated server is needed to run amp-sync.
Correct Answer: D
QUESTION 13
Which Cisco ESA predefined sender group uses parameter-matching to reject senders?
A. WHITELIST
B. BLACKLIST
C. UNKNOWNLIST
D. SUSPECTLIST
Correct Answer: B
QUESTION 14
A network engineer wants to deploy a virtual cisco ESA and wants protection against email-based threats, email encryption, and clustering. Which software license bundle must the network engineer purchase to access these components?
A. cisco email security Premium
B. cisco email security Hybrid Essential
C. cisco email security advansed
D. cisco email security Gateway
Correct Answer: A
QUESTION 15
Which type of server is required to communicate with a third-party DLP solution?
A. an ICAP-capable proxy server
B. a PKI certificate server
C. an HTTP server
D. an HTTPS server
Correct Answer: A
QUESTION 16
Which Cisco technology is a customizable web-based alerting service designed to report threats and vulnerabilities?
A. Cisco Security Intelligence Operations
B. Cisco Security IntelliShield Alert Manager Service
C. Cisco Security Optimization Service
D. Cisco Software Application Support Service
Correct Answer: B
QUESTION 17
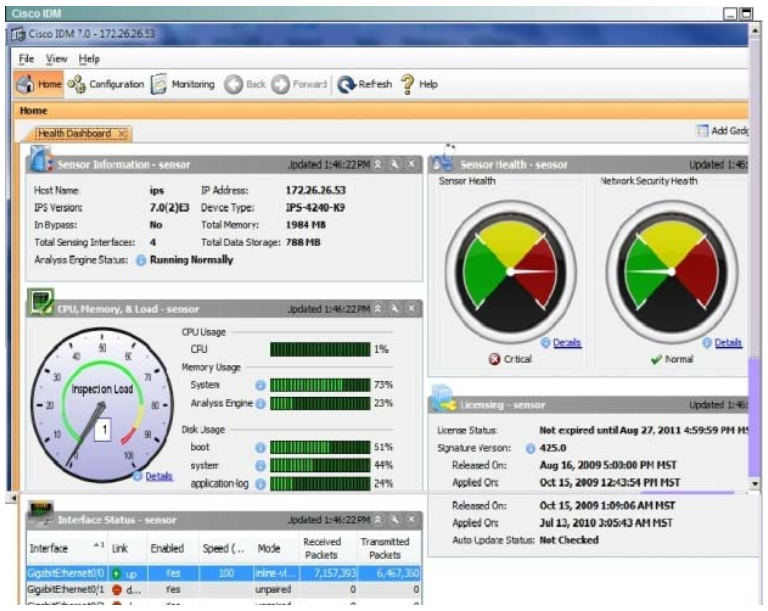
Which three statements about the Cisco IPS appliance configurations are true? (Choose three.)
A. The maximum number of denied attackers is set to 10000.
B. The block action duraton is set to 3600 seconds.
C. The Meta Event Generator is globally enabled.
D. Events Summarization is globally disabled.
E. Threat Rating Adjustment is globally disabled.
Correct Answer: ABC
QUESTION 18
What is the correct deployment for an IPS appliance in a network where traffic identified as threat traffic should be blocked and all traffic is blocked if the IPS fails? 300-210 dumps
A. Inline; fail open
B. Inline; fail closed
C. Promiscuous; fail open
D. Promiscuous; fail closed
Correct Answer: B
QUESTION 19
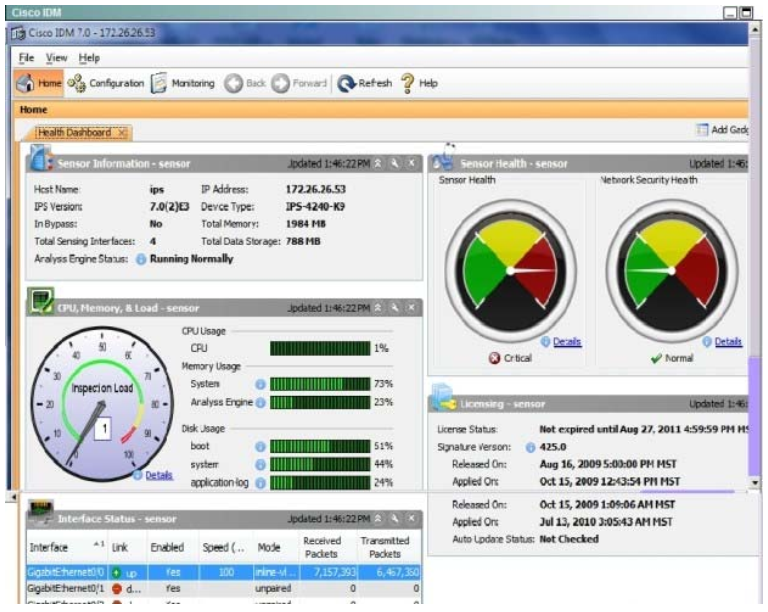
Which signature definition is virtual sensor 0 assigned to use?
A. rules0
B. vs0
C. sig0
D. ad0
E. ad1
F. sigl
Correct Answer: C
QUESTION 20
Which port is used for CLI Secure shell access?
A. Port 23
B. Port 25
C. Port 22
D. Port 443
Correct Answer: C
QUESTION 21
An ASA with an IPS module must be configured to drop traffic matching IPS signatures and block all traffic if the module fails. Which describes the correct configuration?
A. Inline Mode, Permit Traffic
B. Inline Mode, Close Traffic
C. Promiscuous Mode, Permit Traffic
D. Promiscuous Mode, Close Traffic
Correct Answer: B
QUESTION 22
Which Cisco monitoring solution displays information and important statistics for the security devices in a network?
A. Cisco Prime LAN Management
B. Cisco ASDM Version 5.2
C. Cisco Threat Defense Solution
D. Syslog Server
E. TACACS+
Correct Answer: B
QUESTION 23
Which three options are valid event actions for a Cisco IPS? (Choose three.)
A. deny-packet-inline
B. deny-attack-reset
C. produce-verbose-alert
D. log-attacker-packets
E. deny-packet-internal
F. request-block-drop-connection
Correct Answer: ACD
QUESTION 24
During initial configuration, the Cisco ASA can be configured to drop all traffic if the ASA CX SSP fails by using which command in a policy-map?
A. cxsc fail
B. cxsc fail-close
C. cxsc fail-open
D. cxssp fail-close
Correct Answer: B
QUESTION 25
Which set of commands changes the FTP client timeout when the sensor is communicating with an FTP server?
A. sensor# configure terminal
sensor(config)# service sensor
sensor(config-hos)# network-settings
sensor(config-hos-net)# ftp-timeout 500
B. sensor# configure terminal
sensor(config)# service host sensor(config-hos)# network-settings parameter ftp sensor(config-hos- net)# ftp-timeout 500
C. sensor# configure terminal
sensor(config)# service host
sensor(config-hos)# network-settings
sensor(config-hos-net)# ftp-timeout 500
D. sensor# configure terminal
sensor(config)# service network
sensor(config-hos)# network-settings
sensor(config-hos-net)# ftp-timeout 500
Correct Answer: C
QUESTION 26
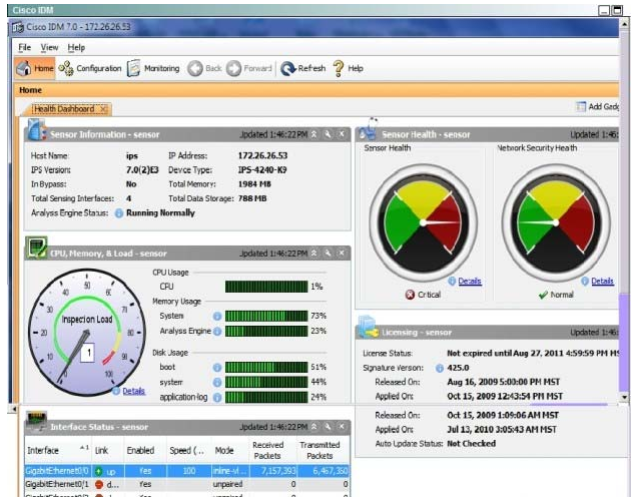
What is the status of OS Identification?
A. It is only enabled to identify “Cisco IOS” OS using statically mapped OS fingerprinting
B. OS mapping information will not be used for Risk Rating calculations.
C. It is configured to enable OS mapping and ARR only for the 10.0.0.0/24 network.
D. It is enabled for passive OS fingerprinting for all networks.
Correct Answer: D
QUESTION 27
Which three zones are used for anomaly detection? (Choose three.)
A. Internal zone
B. External zone
C. Illegal zone
D. Inside zone
E. Outside zone
F. DMZ zone
Correct Answer: ABC
QUESTION 28
300-210 dumps What are the initial actions that can be performed on an incoming SMTP session by the workqueue of a Cisco Email Security Appliance?
A. Accept, Reject, Relay, TCPRefuse
B. LDAP Verification, Envelope Sender Verification, Bounce Verification, Alias Table Verification
C. Recipient Access Table Verification, Host DNS Verification, Masquerading, Spam Payload Check
D. SMTP Authentication, SBRS Verification, Sendergroup matching, DNS host verification
Correct Answer: A
QUESTION 29
Which signature engine is responsible for ICMP inspection on Cisco IPS?
A. AIC Engine
B. Fixed Engine
C. Service Engine
D. Atomic IP Engine
Correct Answer: D
QUESTION 30
Refer to the exhibit.
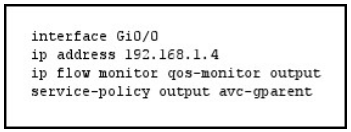
What are two facts about the interface that you can determine from the given output? (Choose two.)
A. A Cisco Flexible NetFlow monitor is attached to the interface.
B. A quality of service policy is attached to the interface.
C. Cisco Application Visibility and Control limits throughput on the interface.
D. Feature activation array is active on the interface.
Correct Answer: AB
Why Choose lead4 pass?
High quality IT learning materials offered by the best provider leads4pass. From the following picture, you can see there is a difference between leads4pass and other brands. Other brands started earlier, but the questions are not the latest and it is very expensive. leads4pass provide the cheapest and newest questions with high pass rate.

The Following Are Some Reviews From Our Customers:
Get the best Cisco CCNP Security 300-210 dumps exam practice materials in PDF format free download from leads4pass. Helpful newest Cisco CCNP Security https://www.leads4pass.com/300-210.html dumps pdf training resources which are the best for clearing 300-210 exam test, and to get certified by Cisco CCNP Security. 100% success and guarantee to pass Cisco 300-210 exam.
Useful Cisco CCNP Security 300-210 dumps vce youtube demo:
https://youtu.be/smQmOmQulh4



